Internet stuff opens up a new universe of connectivity and smart devices that can work together to provide virtually unlimited capabilities and take advantage of these new features to personalize. The value of the Internet of Things is mostly derived from the individual features of products and services to customers, and the direct need for custom features. The biggest challenge of the Internet of Things will come in the protection of confidential information from unauthorized access and authorized access, only our comfortable information disclosure.
Fortunately, there are ways in which senders and receivers that authenticate our confidential information and communications are authenticated with whom we want to share information securely. However, this method involves a large amount of mathematics, the core of complex encryption algorithms. Fortunately, these mathematical algorithms can be buried inside us using the intranet so that we don't need to understand how the password is "how" to implement the details of the electronic device. However, it also helps to have a bit of background for these encryption algorithms for us as well as the security that can be provided, and we need to protect what we do in the brave new IoT world.
Figure 1: The Internet of Things requires advanced security to protect our privacy.
Secure communication
One of the earlier uses of encryption involves replacing the entire alternative code with one letter in place of another. If the receiver knows the alternative formula, perhaps simply changing the cypher where the "A" in the message will become "B" and "B" becomes a "C" in the message, which makes it easy to decode the message. Anyone who sees encrypted messages is not aware of the content unless they also know the secret key. Unfortunately, these simple types of passwords prove easy to decode with a few trial error attempts.
In the modern digital world, we can use more sophisticated methods to encrypt mail—the method of using the powerful processing power of a computer or even Mcu. These methods still use a secret key and encryption algorithm of the familiar concept to encrypt the message, but digital signal processing techniques (encryption math functions) can also be used, making it difficult to decrypt the message without a secret key. Unfortunately, the processing power available to modern computers can also make it easy to over-simplify interrupt code. Therefore, there is a need to have to create code that is too complex for breaking even "brute force" (trial and error) methods for even powerful digital computers.
The common way to create difficult-to-break cryptographic functions using mathematical methods is to find a mathematical problem that is difficult to solve, but it can be solved more easily with a "tip". As an example, consider two very large prime numbers of the product. It can be proved that if you only know the product, it is the two main factors that take time to calculate and determine. It can also be shown that the message can be encrypted, it can only be decrypted very quickly if the two main factors known (ie, implied) are used in this way. And on this basis, these facts allow you to publish the product as your "public key". Anyone who wants to send you a secure email can use the knowledge, only those who know the prime factor can decrypt the message. If this person also has a public key that can respond to their public key to encrypt your message, their message leads to a secure communication channel! A common use of this secure channel is that the send key can be used as a shared secret that is still very robust to other encryption algorithms, but requires computing power consumption lower than the public key system.
Figure 2: Public and private security keys will be used to protect our privacy in the virtual IoT world
Message authentication
Because anyone can send encrypted mail, a concern around the encryption process verifies that the sender says they are. Fortunately, it is a way to verify the sender's usage public key. You can return the encrypted message to the sender, including a random number, and ask them to send you the number behind the encrypted message. If the random number is received and the correct sender has proven that they know how to decrypt the message associated with their public key, the only thing they can do. Therefore, you can now ensure that the message is true and from the specified sender.
Message integrity
In addition, it is essential to ensure that messages are not intercepted and that third parties are not modified. If the message is sent as a text in an email, flipping a few bits will usually make the text unreadable, so you might think that all such activities will be noticeable. However, consider an example that involves code updates for embedded MCUs. Flipping some BITs will dramatically change the final code and keep the MCU doing its job. If it's working to adjust the temperature in a large communication switch, you can imagine the trouble that can happen. Therefore, it is necessary to find a way to ensure the integrity of the message, so tampering can be detected immediately.
A common method of doing this involves generating a tag (often called a message authentication code or MAC) that, in a complex way, depends on all the bits in the body of the message. Think of it as more involved in the parity of the version, detecting if there is a bit in the flip. This tag is added and encrypted and the body of the message. The receiver can decrypt the message (including the tag) and then regenerate the tag from the decrypted message body. If the regenerated tag matches an embed in the message it has not been tampered with. Please note that the MAC requires a shared key to ensure that no one else can generate the mac.
Industry standards are used to create a range of information security standards. The Advanced Encryption Standard (AES) established by the National Institute of Standards and Technology (NIST) is one of the most popular and commonly implemented with block sizes of 128, 192, and 256 bits. Both the sender and the receiver use the same key—the so-called symmetric beat, instead of using a different key by the sender and the receiver's public key system—so it is usually using a public key message exchange, Often just a single session.
MCU vendors have made it easy to implement AES security features, including dedicated hardware inside the microcontroller. For example, the Texas Instruments MSP430FR5969 microcontroller family includes dedicated hardware AES to accelerate the encryption and decryption required for peripheral implementations. Peripherals also include national memories that are stored during encryption or decryption operations (long series of changes, replacements, interchanges, Xor all security keys) and security keys. The design engineer simply loads the 128-bit block into the state memory and the specified function — encryption or decryption — will start automatically. The resulting encrypted or decrypted output is read from the state memory.
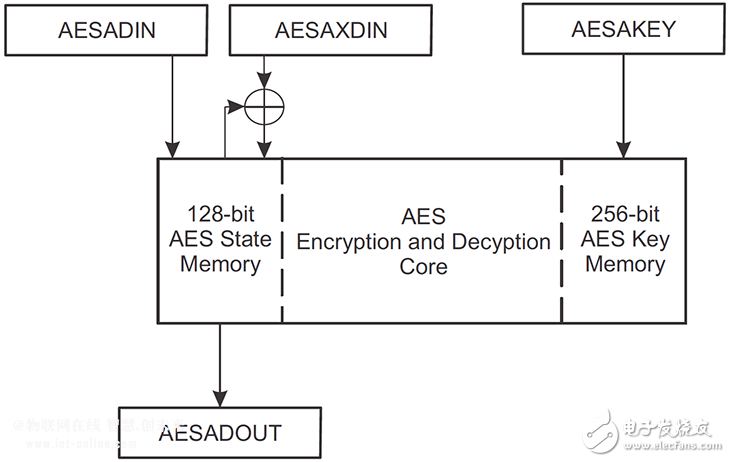
Figure 3: AES Hardware Accelerator at Texas Instruments MSP430FR59xx Microcontroller. (Source: Texas Instruments)
Similar hardware accelerators can find other common encryption features such as the MAC feature used to generate authentication digests. The most common MAC algorithm is the Secure Hash Function (SHA) standard established by NIST. The hardware accelerator is also available for sand at Mcu. For example, Freescale Dynamics K6x family devices offer a variety of standards for hardware-accelerated coprocessors, including AES and sand. The coprocessor can run independently from the CPU and use a memory-mapped interface so that it can be buffered as cryptographic accelerator units (CAU) of commands and data. Because this unit acts as a coprocessor architecture, it can operate without CPU intervention and can greatly improve efficiency if encryption is a large percentage of processing requirements.
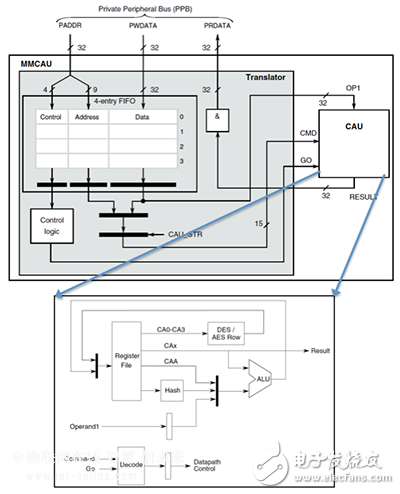
   Figure 4: Freescale Dynamics K60 Microcontroller Cryptographic Accelerator Peripherals (Source: Freescale Semiconductor)
Other ways to implement security features
In addition to providing hardware-accelerated peripherals and coprocessors, manufacturers also offer other security features to help protect our privacy in the IoT universe. For example, Atmel offers special secure memory devices like the AT88SC0204CA. It uses symmetric mutual authentication, data encryption, and MAC operations to provide a secure place to access sensitive information stored in the system through a standard microcontroller serial interface. There is an additional tamper detection circuit, and this information is still safe from hardware attacks trying to access security information.
Another method is in more specialized forms that can be implemented in conjunction with a microcontroller to implement security functions. The Maxim produces a range of devices that use Sand 256 hardware to securely transfer data across standard 1-wire interfaces. The peripheral Identifier of the MCU, like the Maxim DS24L65, converts the standard I2C interface into a secure 1-wire interface that can be connected to various secure 1-wire peripherals such as the Maxim DS28EL22, the Shangsha 256 MAC-based hardware chip 2Kbit EEPROM and guaranteed The only 64-bit ROM ID code. Host-to-slave authentication is used to protect the modified nonauthenTIc host in the DS28EL22 user memory. The Changsha-256 MAC, DS28EL22 generation, is calculated from user memory, on-chip secrets, host random challenges, and 64-bit ROM ID for very robust security. Note that these devices can be included in a standard set of peripheral I2C connections, such as smart sensors, which authenticate the sensor from the intended manufacturer and they have not been tampered with. This is especially important when sensor readings are used to generate utility and similar “pay-as-you-go†revenue.
in conclusion
The method used to protect confidential data—Mcu with dedicated encryption supports common security algorithms, shutting down the chip encryption memory to store sensitive information or hardware-level authentication to ensure that the peripherals are authentic.
Dongguan Deli Plastic Co.,Ltd is a manufacturer specialized in the research, development ,plastic injection mould and making mass production with well-equipped facilities and strong technical force.
Our products are extensively used in household industry/electronic industry/automobile industry/building industry and other industries.
We have rich experience on one-stop solution, provide various services from new product design,prototype,mold making,mass production,assembly and logistics. The most important advantage is we have our own R&D team to help clients to turn ideas into actual parts. All of these engineers and designers have over 15 years experience in these plastic products fields.
We have a strict quality control system, an excellent management team and also a dedicated sales force, enable us to fulfill our commitment in high quality products and outstanding services.
If you are looking for a trustworthy supplier of customized items, please do not hesitate to contact us. We are always striving to establish a win-win partnership with customers from all over the world and help our partners to stay one step in front of your competitors.
Rotating Fan,Small Rotating Fan,Rotating Fan Tower,Fan Rotation For Summer
Guangdong Aiyimi Electronic Technology Co., Ltd. , https://www.nbminifan.com