KENTON WILLISTON
IoT security is a thorny issue. Protecting personal devices is not enough. At the same time, developers must use existing embedded systems and IT systems in the field to protect their device connections.
Blockchain is an effective way to protect these network connections, but it is difficult to implement in traditional systems. In order to solve this problem, SPARKL and other companies created corresponding solutions. Even if the network contains untrusted devices, the solution allows new devices that support the blockchain to interoperate with existing devices on end-to-end security.
IoT security challenges
Many embedded and IoT products are deployed in the market. The scale, status, and computing performance of these products are excellent. However, end users have no control over many aspects of network services. In this situation, traditional IT security measures such as local anti-virus software or enhanced network infrastructure appear to be impractical.
For these markets, security mechanisms must be based on IoT devices and protocols, not aftermarket software. This is the significance of introducing blockchains.
Bitcoin and blockchain
If you have heard of blockchain, it may be due to Bitcoin. Bitcoin is a digital cryptocurrency that relies on the blockchain to save previous transaction records.
The concept of blockchain is narrow and broad. In a narrow sense, blockchain refers to the special method used by Bitcoin to create, maintain, and protect transaction records.
Broadly speaking, blockchain refers to the use of distributed ledgers to protect and maintain the transaction ledger that each stakeholder and authorized individual has the right to view. In some cases, the "Distributed Distributed Ledger" (MDL) can be used interchangeably with the blockchain, but the meaning of the two is not exactly the same.
Each blockchain is a common distributed ledger, which means that each blockchain is an independent, transparent, and permanent database that can exist in multiple areas at the same time, but not all MDLs are blocks. chain.
In simple terms, blockchain is a continuous transaction ledger.
Each set of transactions (called transaction blocks) is cryptographically protected and links to previous transactions are verified.
Imagine a series of transaction blocks. Each transaction block is connected end-to-end and the name of the "blockchain" comes from: The transaction block is a literal description of the transaction record storage and authentication methods, and each transaction block carries Secure transaction transaction timestamp information and record data are encrypted. Since the hash value of each new transaction block will be based in part on the hash value of all previous transaction blocks, the blockchain cannot be edited and modified without the quick and obvious tamper approach, and only the majority agrees. The record can be modified (if the record is fully accessible).
Early success signal
A year ago, Intel® released its own proprietary blockchain platform and has demonstrated how blockchain and the Internet of Things track the movement of seafood in the supply chain (Figure 1).
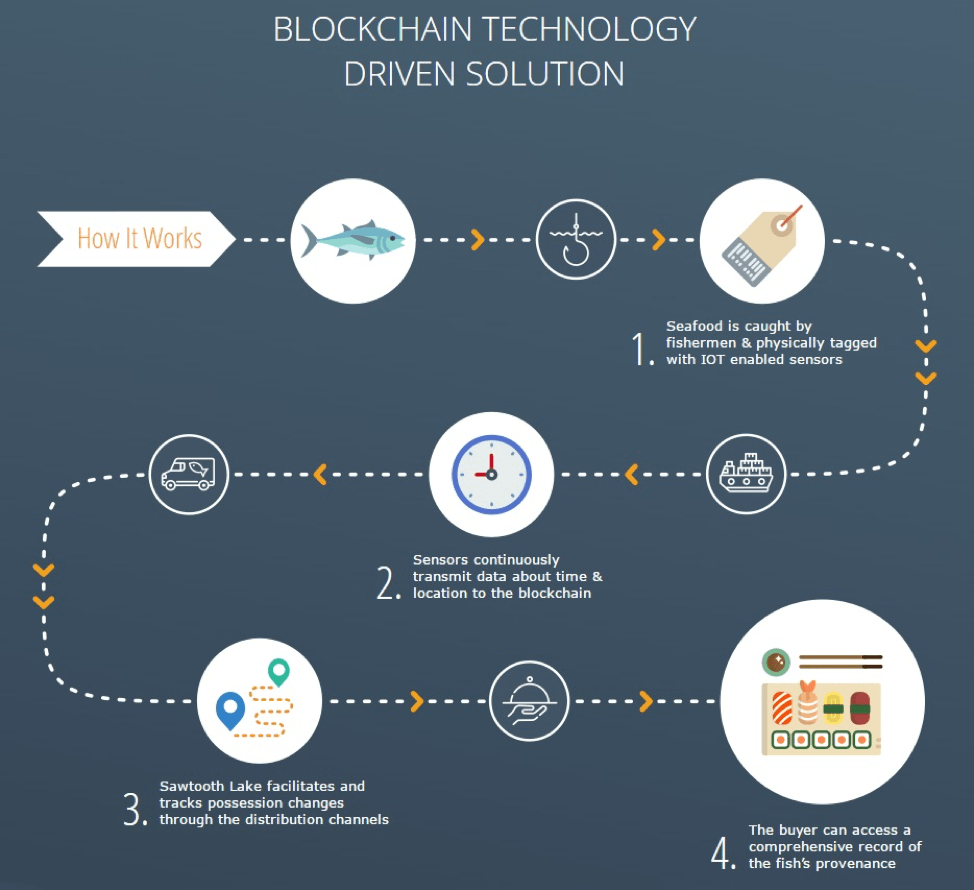
Figure 1. Use blockchain technology to monitor the entire process of seafood from first capture to final purchase.
By monitoring the movement of the product in the sales network, the supplier or seller can quickly and accurately determine the source of any contaminated food, or identify the person who handles the product at a given time. In the event of a product recall or contamination incident, blockchain-based ledgers allow companies to find out which stores sell which products and find customers who buy the products.
In addition, by assigning unique identifiers to physical products to ensure the authenticity of each specific device, it can be assessed whether blockchain technology can be a way to protect IoT devices. Currently, the IoT device is controlled by the central server infrastructure, which makes the device vulnerable to attacks. The decentralized nature of blockchain technology can reduce the probability of IoT devices encountering risks and can help protect products in the development phase.
Solve deployment issues
Blockchain technology has the potential to solve serious problems in the world of IoT, but it can only be successful if it is implemented correctly. Developers must understand the needs of customers, the solutions that customers have already deployed to meet these needs, the effectiveness of previous solutions, and the identities of different stakeholders in a given environment.
For example, when deploying IoT sensors to monitor warehouse temperatures, who needs access to records that ensure the ambient temperature is normal? Who should receive a warning if the temperature exceeds the threshold? Is the Internet of Things solution able to adjust room temperature or is it limited to warnings?
Blockchain technology can't cure all diseases. If the problem is not clearly stated and is constrained to be consistent with the details of the existing solution, blockchain technology cannot automatically provide a solution to the problem.
Some traditional embedded systems may be able to support blockchain protected IoT products. However, some systems may need to be upgraded or replaced. Developers will have to solve the problem of moving from a centralized server infrastructure to a decentralized model, and the decentralized model can handle the input of tens, hundreds, or even thousands of devices. If you want to successfully implement blockchain, you need a flexible and scalable solution.
Now let's take a look at SPARKL, whose unique features allow legacy systems to interface with smart blockchain support strategies and complex control systems.
What is SPARKL?
SPARKL includes two key components: SPARKL sequencing engine and Clear Box configuration system. Clear Box was specifically designed to support simultaneous interaction of multiple systems and provide a single point of access for all the information developers need to achieve system collaboration, even though these systems typically do not communicate with each other.
Clear Box is very flexible and can support the implementation of multiple blockchains at the same time. It can also invoke third-party services or applications (Figure 2). It also allows fine-grained permission settings to ensure that only users who are certain to view a particular data set have access.
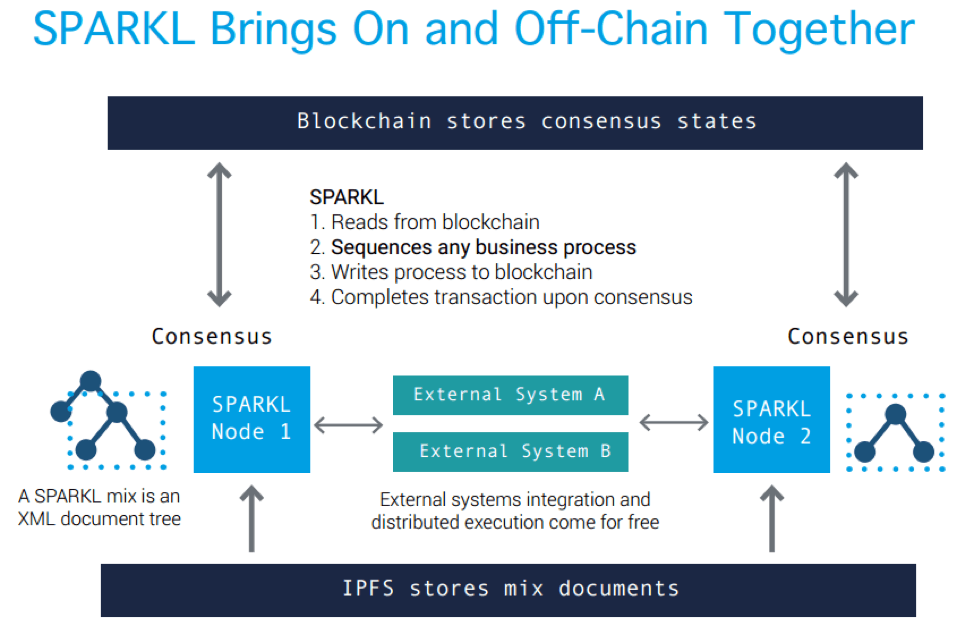
Figure 2. How SPARKL interacts with external blockchain nodes.
When considering the deployment of IoT devices and blockchain technologies, that is, when dealing with the difficulties associated with traditional systems, the flexibility of Clear Box can solve this major problem. The Clear Box and SPARKL sequencing engines are not trying to implement a completely new control system and then building a unified hardware and software solution that can handle each use case. Instead, they can communicate with existing solutions and collect data from a large number of resources. And execute the instructions that the end user has defined. If the Clear Box is a solution to define a strategy or behavior, then the SPARKL Sequencing Engine drives these strategies and behaviors to run smoothly throughout the system.
In a proof of value (PoV) published by SPARKL, it explains how to use blockchain technology and its own services to develop smart contracts for the reinsurance market. SPARKL is compatible with a variety of distributed ledger projects, including BigchainDB, HyperLedger, and Intel® Sawtooth Lake, which can be used for reinsurance (Figure 3).
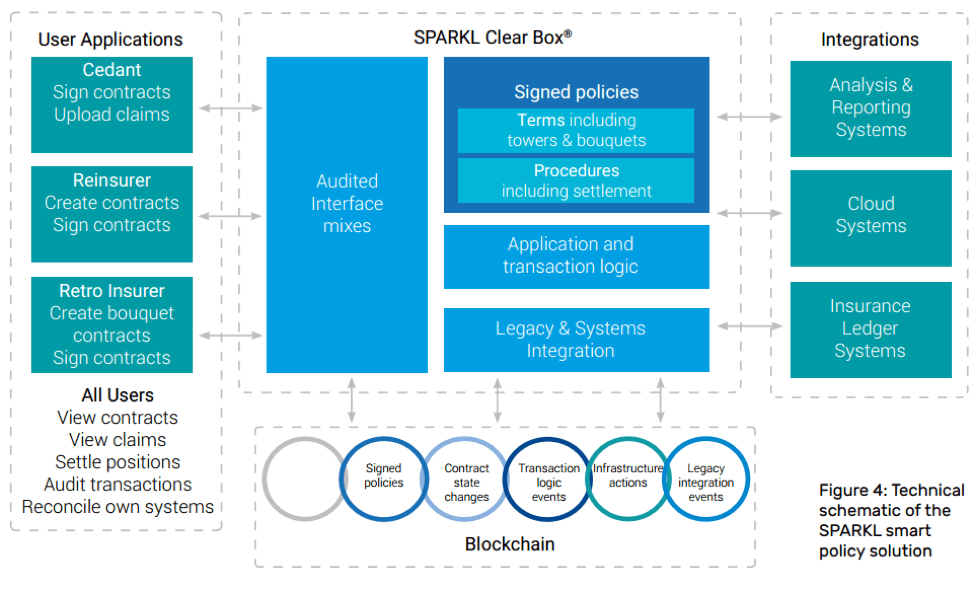
Figure 3. SPARKL's intelligent policy system is based on Sawtooth Lake and is designed to meet the needs of all stakeholders in every part of the process.
Sawtooth Lake is a modular, distributed ledger platform that uses a versatile and scalable design that supports a range of consensus models. In this article, consensus is the process of establishing consensus among systems that do not trust each other.
The goal is to create a set of intelligent strategies to account for the different trust relationships between participants, the interface between traditional and non-traditional systems, support for a complete automated strategy workflow, and record in a transparent manner that all parties can see transaction. For smart strategies to work effectively, they must be able to assess complex conditions, properly group claims, apply any policy restrictions, calculate and process premium payments, and update the transaction ledger accordingly at each of these steps.
The result of this process is not to stick another "Tribo" to the barely operating infrastructure, but if it is done correctly, SPARKL can be used to connect legacy systems with the latest systems and establish new smart contracts and tactics based on blockchain. In order to force the automatic execution of the contract, all stakeholders are provided with the documents they need for the purposes of keeping records and regulatory supervision.
Rectifier bridge is to seal the rectifier tube in a shell. Points full bridge and half bridge. The full bridge connects the four diodes of the connected bridge rectifier circuit together. The half bridge is half of four diode bridge rectifiers, and two half bridges can be used to form a bridge rectifier circuit. One half bridge can also be used to form a full-wave rectifier circuit with a center-tapped transformer. Select a rectifier bridge to consider. Rectifier circuit and operating voltage.
Bridge Rectifier,Original Bridge Rectifier,Full Bridge Rectifier ,Diodes Bridge Rectifier,Single Phase Rectifier Bridge, Three Phase Bridge Rectifier
YANGZHOU POSITIONING TECH CO., LTD. , https://www.pst-thyristor.com