Introduction Security has always been a shadow of the advantages of WLAN's flexibility and convenience, and it has become the biggest obstacle hindering WLAN from entering the field of informatization applications. International standards have adopted WEP, WPA, 802.1x, 802.11i, VPN and other methods to ensure the security of WLAN, but they have not fundamentally solved the security problem of WLAN. In May 2003, China proposed the national standard for wireless local area networks GB15629.11 and introduced a new security mechanism—WAPI, which made WLAN security issues the focus of attention again. The WAPI mechanism has been reviewed and approved by the IEEE RegistraTIon Authority authorized by ISO / IEC, and the Ether Type Field (IEEE EtherType Field) 0x88b4 used for the mechanism has been assigned. The only ether type number.
WAPI security mechanism WAPI (WLAN AuthenTIcaTIon and Privacy Infrastructure) is composed of WAI (WLAN AuthenTIcation Infrastructure) and WPI (WLAN Privacy Infrastructure). Among them, WAI uses an elliptic curve-based public key certificate system, and wireless client STA and access point AP perform two-way identity authentication through an authentication server AS. In terms of confidentiality of the transmitted data, WPI uses the symmetric cryptographic algorithm provided by the Office of the National Commercial Password Management Committee for encryption and decryption, which fully guarantees the security of data transmission.
WAPI fully considers the market application. According to the different situations of wireless LAN applications, it can work in different modes such as single-point and centralized, and can also be combined with the existing operator system to support large-scale carrier-level services. In addition, users have different usage scenarios, and the implementation and working methods of WAPI are slightly surprised. WAPI user usage scenarios include the following:
1. Enterprise-level user application scenarios: AP and independent AS (authentication server), internal ASU (authentication service unit), to achieve multiple AP and STA certificate management and user identity authentication;
2. Application scenarios for small companies and home users: with AP, ASU can reside in the AP;
3. Application scenarios of public hotspot users: AP, ASU reside in the access control server;
4. Ad hoc network user application scenario: no AP, each STA is equivalent in application, and uses a shared key to achieve authentication and confidentiality.
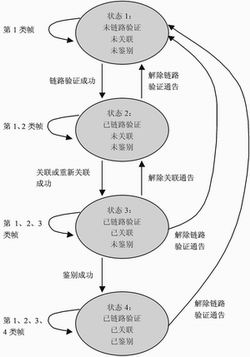
Figure 1 State transition diagram
WAI
State transition diagram of STAs related to WAI Figure 1 shows the state transition diagram of STAs related to WAI. Compared with 5.5 of ISO / IEC 8802.11-1999, the state diagram changes the original "identification" to "chain" "Road verification", in addition to the "authentication status" dedicated to handling the WAI process. In this way, the STA needs to maintain a total of three state variables: link verification state, association state, and authentication state, which determines that the STA will have four local states, as shown in states 1 to 4. The WAI authentication process between STA and AP is in state 3.
Structure of authentication system Figure 2 describes the relationship and information exchange process between the authentication requester, the authenticator and the authentication service entity. Here we first introduce a few important concepts that will help to understand the structure of the authentication system.
Discriminator entity AE: resides in the AP and provides authentication operations before accessing the service.
Authentication requester entity ASUE: resides in the STA and needs to be authenticated by the authentication service unit ASU.
Authentication service entity ASE: resides in ASU and provides mutual authentication for the authenticator and authentication requester.
In FIG. 2, the controlled port of the discriminator is in an unauthenticated state, the discriminator system refuses to provide services, and the discriminator entity uses the uncontrolled port to communicate with the authentication requester.
Controlled and uncontrolled ports can be two logical ports connected to the same physical port. All data that passes through the physical port can reach the controlled port and the uncontrolled port, and the actual flow of data is determined according to the authentication status.
Controlled port: Only when the authentication status of the port is authenticated, protocol data is allowed to pass. The data port provided by the AP that can be used only by the authenticated STA is a controlled port.
Uncontrolled port: The transmission of protocol data is not restricted by the current authentication status. The port where the AP provides the STA to connect to the authentication service unit ASU is an uncontrolled port.
It should be noted that, in addition to the authentication data, the network protocol data exchange between the AP and the STA in the system is achieved through one or more controlled ports. The controlled port status is determined by the system identification control parameters.
Another important concept is the authentication service unit ASU. As mentioned earlier, in the entire WAI authentication process, ASU acts as a third party to provide authentication services. In addition, ASU is also responsible for the issuance, certification, and revocation of certificates for STAs and APs. An ASU can manage one or more BSSs. Within the management scope of the same ASU, the STA and the AP need to pass the ASU to achieve two-way authentication of the certificate.
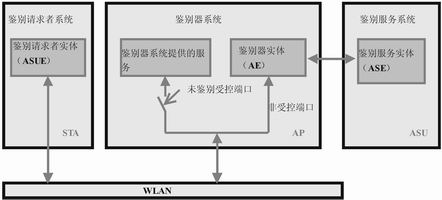
Figure 2 Identification system structure
WAI authentication infrastructure In BSS, when an STA associates or re-associates with an AP, mutual identity authentication must be performed. If the authentication is successful, the AP allows the STA to access, otherwise it releases its link authentication. The entire authentication process includes certificate authentication, unicast key negotiation and multicast key announcement.
The authentication data packet between the STA and the AP is transmitted using the WAPI protocol with an Ethernet type field of 0x88B4. The authentication data packet between the AP and ASU is transmitted through the UDP socket with the port number 3810.
In the whole process of WAI, several encryption / decryption and message digest algorithms are involved, which can be summarized as shown in Table 1.
WAI-based security access control classification According to different types of WLAN, WAI-based security access control can be classified as follows.
BSS (with AP)
The typical example of WAI uses public key cryptography to realize mutual identity authentication between STA and AP. After successful certificate authentication, it is divided into unicast key negotiation and multicast key announcement.
IBSS (Ad Hoc, no AP)
WAI uses a shared key to complete mutual identity authentication between STAs. Each STA in the network agrees on a shared key, and the user accesses the network by setting (inputting) the shared key and exchanges information with other users. The user enters the shared master key.
WDS mode
WAI uses a shared key to complete mutual identity authentication between STAs. Each STA in the network agrees on a shared key, and the user accesses the network by setting (inputting) the shared key and exchanges information with other users. The user enters the shared master key.
WPI
WPI adopts the SSF43 symmetric block encryption algorithm for WLAN approved by the Office of the National Password Management Committee to encrypt / decrypt the MSDU of the MAC sublayer. There are two working modes: OFB mode for data privacy and integrity check CBC-MAC mode.
WPI encapsulation process When data is sent, the WPI encapsulation process is:
1. Encrypt the MSDU (including SNAP) data by using the encryption key and the data packet sequence number PN through the encryption algorithm working in OFB mode to obtain the MSDU ciphertext;
2. Use the integrity check key and the data packet sequence number PN to calculate the integrity check data through the check algorithm working in the CBC-MAC mode to obtain the integrity check code MIC;
3. After encapsulation, framing is sent.
WPI decapsulation process When data is received, the WPI decapsulation process is:
1. Determine whether the data packet serial number PN is valid, if it is invalid, discard the data;
2. Use the integrity check key and the data packet sequence number PN to perform local calculations on the integrity check data through the check algorithm working in the CBC-MAC mode. If the calculated value and the integrity check code in the packet If the MIC is different, the data is discarded;
3. Use the decryption key and the data packet sequence number PN to decrypt the MSDU ciphertext in the packet through the decryption algorithm working in OFB mode to recover the MSDU plaintext;
4. After decapsulation, submit the MSDU plaintext to the upper layer for processing.
Conclusion At present, we have implemented the WAPI mechanism of STA with software, and the operation results can fully meet the requirements of the GB15629.11 standard. In addition, we also used the hardware description language Verilog HDL to describe the WPI packaging and de-encapsulation process RTL, and optimized it from the perspective of digital circuit design. Overall, the WPI hardware simulation results show a strong advantage over WPI software running in time, which is undoubtedly a very important point to ensure the high speed of wireless LAN data communication. Of course, WPI software can be combined with the driver, reflecting the characteristics of low cost and easy maintenance. For WAI, the entire process is before the network protocol data communication between AP and STA, so the time requirement is slightly inferior, and the process is relatively complicated. The author believes that it is more suitable to be implemented in software.
Sdec 0-20Kw Diesel Generator,Sdec Soundproof Power Generator,Sdec Mobile Power Generator,Sdec Canopy Power Generator
Shanghai Kosta Electric Co., Ltd. , https://www.ksdgenerator.com