1 Introduction
This article refers to the address: http://
At present, theft of cars has occurred. The navigation of the vehicle is also a GPS-based positioning display. It only needs to receive more than two of the 24 geosynchronous satellites (the more accurate), the current vehicle can be displayed. Location, but it can only accept information without a launch function, so it has no effect on theft. This device is easy to use. When W1 is closed, the owner can leave the car; when coming back, disconnect W1. It is hijacked during driving and closes W2. Moreover, the cost is low, and there is no need to pay various alarm fees, which is suitable for medium and low-end car installation.
2 Working principle
Anyone who is familiar with the mobile phone knows that the mobile phone has a positioning function, and sends the specified letter to a specific number, and then can get a reply to the short message to inform you of the current location. Of course, it is implemented through the mobile communication network platform.
For the mobile communication platform, the specified letter is: ZJ; the specific number is: 05,058. When the ZJ letter is sent to 05558, you can get a text message sent back from the mobile communication network to inform you of the current location information. This kind of position information is usually in the form of polar coordinates (Ï, θ), which is based on a famous building nearby, and then the distance between your current position and the pole is the radius Ï, and the diameter is given. The direction θ is used for positioning. How to use the mobile communication network to realize the positioning function of the car? Figure 1 shows the working diagram of the technology.
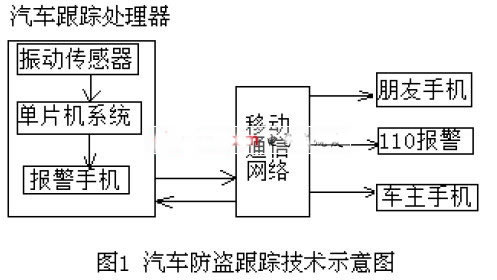
It is a system composed of a car tracking processor, a car owner, and the like, and then uses a mobile communication network platform. The core part is a "car tracking processor" installed in a car. The processor consists of a mobile phone, a single chip microcomputer, a vibration sensor, and the like. Usually the sensor does not work. When the owner leaves the car, the sensor starts to work. At this time, if the thief moves the car, the sensor output signal makes the MCU system work, and the ZJ letter is sent to the mobile communication network 05058 through the alarm mobile phone, and gets moved. The location information of the car returned by the network. Then, it is controlled by the single chip microcomputer, and the position information is sent to the owner's mobile phone through the mobile network, thereby showing that the actual position of the car can be known regardless of the position of the owner. When the thief starts the car, the car tracking processor repeats the previous process (one minute to one minute and a half), and informs the owner of the current car position one by one, which plays a role of position tracking.
If the owner is hijacked by the thief during the driving process, just take an insignificant little action and press a hidden small switch to make the car tracking processor repeat the above process regularly. Of course, the recipient of the location information is not the owner. I am my own friends and relatives (if I ask for help from 110, I need to forward it by my friends and relatives, because I haven’t received the SMS yet)! Let them know where they are going and win the shortest rescue time.
3 hardware design
The hardware design here refers to the design of the "car tracking processor", and the main part is the one-chip computer system. Figure 2 shows a simplified hardware design. The MCU uses the most popular and inexpensive small size (20-pin) AT89C2051.
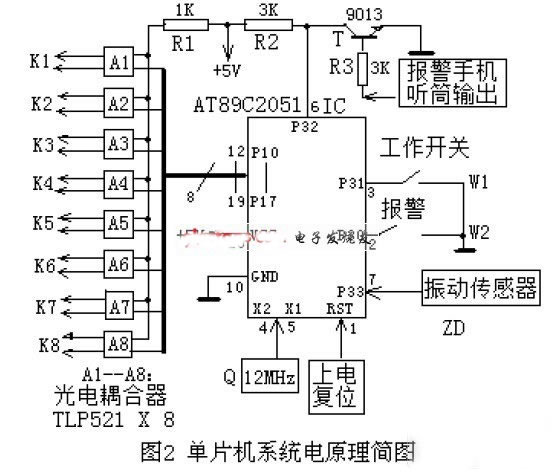
When the owner leaves the car, the work switch W1 should be closed. When the owner is hijacked, the hijacking alarm W2 should be closed. These two switches should be placed in a relatively hidden but easily accessible area. The eight pins of the P1 port (P10-P17) of the AT89C2051 are used to control the on/off of the eight optocouplers of the A1-A8 (the pin is turned on when the pin is low). The advantage of using the optocoupler is that it can function between the circuits. Isolation, because the level of the phone keypad is not the same as the level of the microcontroller system. When the MCU system is initialized, each input and output pin (P10-P17, P30-P33, etc.) is at a high level. When the vibration sensor does not work, it outputs a high level, and the microcontroller does not work. When the car is stolen, the sensor outputs a low level, which triggers the operation of the microcontroller. Controlling A1-A8 through P10-P17 causes K1-K8 to turn on and off respectively, simulating a series of keystrokes of the alarm mobile phone to complete the entire alarm process.
The handset of the alarm phone must be disconnected and heard by the burglar thief. However, its output signal must also be retained and input to R3, 9013 as a reminder signal for the location information of the mobile communication network. The P32 pin of the IC is originally high. When prompted, it goes low, so the MCU controls the alarm phone to send the location information (the owner's mobile phone, friend's mobile phone or forwarding 110, etc.).
Although the alarm phone has 19 keys, we only use 8. See the key labeled K1 - K8 in Figure 3, each key is connected to the corresponding two lines. Because the alarm mobile phone can adopt a variety of styles, the specific keyboard arrangement and the functions of the keys are not the same, and should be treated differently when used. Of course, the programming of the program is also different, which should be noted. The mobile phone we use is the cheapest mobile phone (Band: BiRD_S1160), the mobile phone itself does not need money, pay 500 yuan for the call charge. Each button of the mobile phone has multiple functions, such as K1 can send text messages, etc.; K2 can enter the preset phone book; K3 can be turned off, reverse, etc.; K4, K5 can be turned upside down, etc.; K6 is turned on, confirmed, etc.; K7, K8 can type "ZJ" letters and so on. Due to space limitations, it cannot be exhaustive. Refer to the BiRD_S1160 instruction manual.
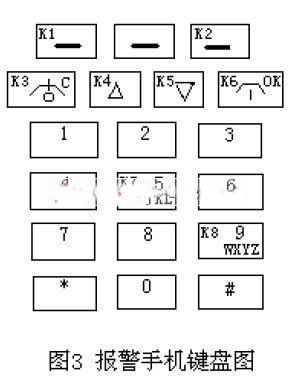
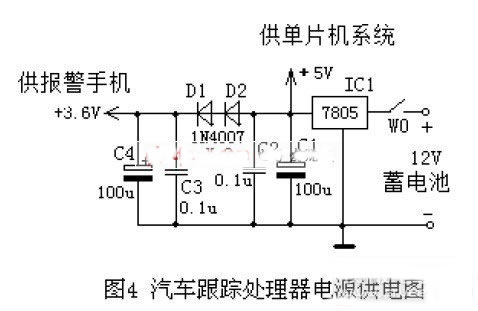
Figure 4 shows the power supply diagram for the car tracking processor. It is supplied by the battery on the car after being stepped down twice. It is firstly regulated by the 7805 to be supplied to the MCU system by 5V, and then reduced by two diodes to 3.6V for the alarm mobile phone.
The "car tracking processor" consisting of alarm mobile phones, single-chip microcomputers, vibration sensors, power supply devices, etc. should be placed in a relatively hidden place inside the car. This connection of the alarm phone does not hinder the original performance and use of the phone. Before using the alarm mobile phone, three phone numbers should be preset in the phone book in the mobile phone: 1: the owner phone, first store the owner's name, and then store the owner's phone number; 2: location information, first store Chinese Location information", then store 05508; 3: alarm phone, first store "Save! AX-33445" (the latter letters and numbers are the car license plate number), and then store the friend's phone number. Just enter the phone book and choose it. The use of different mobile phone function keys is also different. For details on the use of this mobile phone, refer to the BiRD_S1160 instruction manual.
4 software design
The program of this machine is solidified in AT89C2051, which is mainly used to simulate the keystroke process of alarm mobile phone. Figure 5 shows the software block diagram of the car tracking processor.
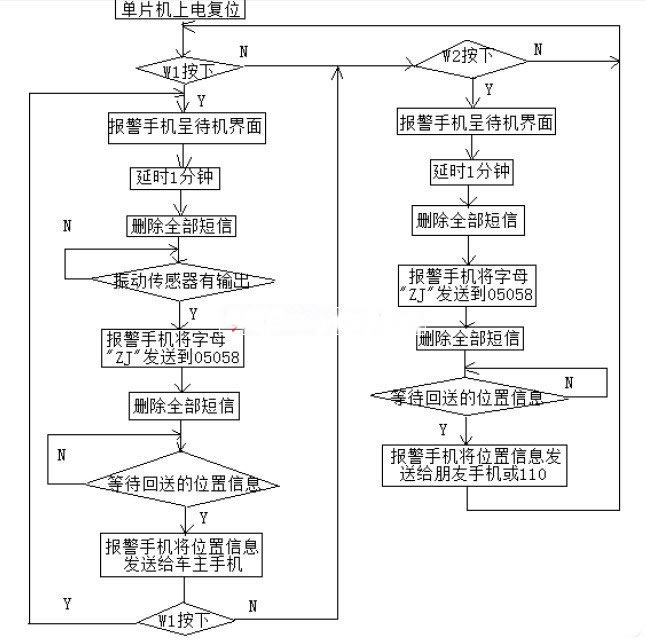
After the power switch W0 is turned on, the program continuously checks whether the buttons W1 and W2 are closed. If W1 is closed, the vehicle enters the car anti-theft system, the alarm phone enters the standby interface, and all the original messages are deleted, so as to avoid erroneous short message output.
A Then check if the vibration sensor has an output? (Is it stolen?), wait for the loop, if so press K7, K8, type ZJ two letters and send it to 05558. Delete all the short messages again, and wait for the location information of the mobile communication return (actually, check if the P32 of the IC is low. If there is a reply, the handset will output a high level and P32 will be low). Then forward the location information to the owner. Then go back and send the next one, about one and a half minutes apart.
The delay of 3 minutes by W1 is reserved for the owner to leave the car. Otherwise, pressing W1 will cause an alarm.
If the owner is hijacked, the alarm can be completed by closing W2. The process is similar to the former, except that the vibration sensor is not used, and the location information is sent to a friend or forwarded 110.
5 Conclusion
When alerting a friend, you can use SMS directory or SMS content.
The former is simple, but the number of words is strictly limited. It is to write "Save! AX-33445" to the name of the person in the phone book, and then fill in the friend's mobile phone number at the corresponding number. When it is sent to a friend's mobile phone, the other party will first see the text message "Save! AX-33445". Rescue operations can be taken; or 110 can be forwarded by a friend's mobile phone, and the license plate number and actual location of the robbed vehicle are continuously informed, and 110 is dispatched to rescue.
The use of SMS content is more complicated. It can't be written and saved. The SMS is stored first. It is called when it is used. Because the mobile phone often receives some messy text messages, it will disturb the original order. The mobile phone does not distinguish these messages. Function, so it can only be written temporarily when sending, so more keys are needed, resulting in complicated hardware and complicated programming process.
The equipment is highly automated and easy to use. When W1 is closed, the owner can leave the car; when coming back, disconnect W1. It is hijacked during driving and closes W2. Moreover, the cost is low, and there is no need to pay various alarm fees, which is suitable for medium and low-end car installation.
Guii Labs Vape,Fume Extra 1500 Puffs ,Disposable Vapor Stick ,Vape Pen Pop
TSVAPE Wholesale/OEM/ODM , https://www.tsvaping.com