Intelligent security technology refers to the informationization of services, image transmission and storage technology. With the development and progress of science and technology and the development of information technology in the 21st century, it has entered a new field, intelligent security. The line between technology and computers is gradually disappearing.
The popularization and application of Internet of Things technology has transformed the security of the city from the simple security protection system in the past to the urban integration system. The city security project covers many fields, including street communities, building buildings, bank post offices, road monitoring, motor vehicles, Police officers, moving objects, boats, etc. Especially for important places, such as airports, docks, water and electric plants, bridge dams, rivers, subways, etc., after the introduction of Internet of Things technology, it can establish a full range of three-dimensional protection through wireless movement, tracking and positioning. It also takes into account the comprehensive system of the overall urban management system, environmental monitoring system, traffic management system, emergency command system and other applications. In particular, the rise of the Internet of Vehicles can track and locate more quickly and accurately in public transportation management, vehicle accident handling, and vehicle theft prevention. You can also get more accurate information on disaster accident information, road traffic information, vehicle location information, public facility safety information, weather information, etc., anytime, anywhere.
The composition of intelligent security technologyThe main connotation of intelligent security technology is the informationization of its related content and services, the transmission and storage of images, the storage and processing of data, and so on. In terms of intelligent security, a complete intelligent security system mainly includes three parts: access control, alarm and monitoring.
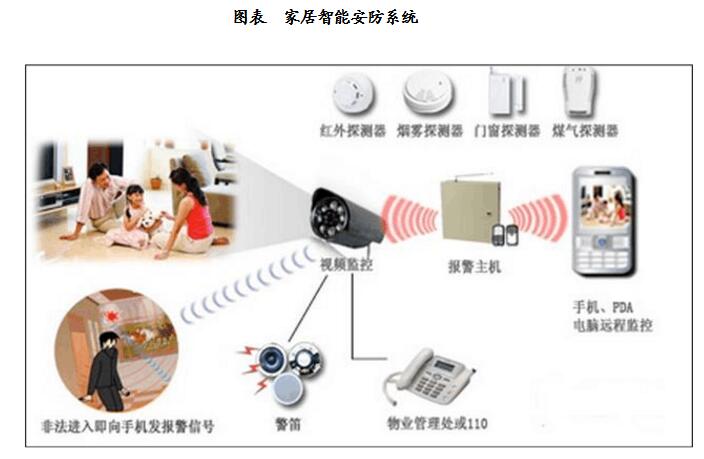
From the product point of view: should have anti-theft alarm system, video surveillance alarm system, entrance and exit control alarm system, security personnel patrol alarm system, GPS vehicle alarm management system and 110 alarm network transmission system and so on. These subsystems can be set up separately, run independently, or centrally monitored by a central control room, and integrated and centrally monitored with other integrated systems.
The burglar alarm system is divided into perimeter defense, defense in the building area, defense in the open area of ​​the unit enterprise, and defense of physical equipment in the unit enterprise. The front-end equipment of the system is various types of alarm sensors or detectors; the terminal of the system is a display/control/communication device, which can be applied with a separate alarm controller or by using an alarm center console. Regardless of the control method used, real-time, reliable and correct review and alarm must be performed on the illegal invasion of the fortified area. Leak alarms are absolutely not allowed, and false alarms should be reduced to acceptable limits. Considering that the duty officer is vulnerable to the threat of force and robbery by the perpetrator, the system should set the emergency alarm button and leave the frequency monitoring alarm system connected with the 110 alarm center for routine monitoring in the main public places and important parts in the building. Image review during recording, recording, and alarming. The front end of the video surveillance alarm system is a variety of cameras, video detection alarms and related ancillary equipment; the terminal equipment of the system is a display / recording / control equipment, conventionally using an independent video surveillance center console or monitoring alarm center console. The video surveillance alarm system for security precautions should be linked with the anti-theft alarm system and the entrance and exit control system, and centrally managed and monitored by the central control room. Independently running video surveillance alarm system, the screen display can be arbitrarily programmed, automatically or manually switched. The screen must have the camera number, address, time, date and other information display, and can automatically switch the live screen to the specified monitor. For important monitoring screens, it should be able to record for a long time. Such systems should have an emergency alarm button and a communication interface with 110 alarm center networking.
The entrance and exit control alarm system is an automatic system that uses modern electronic information technology to perform operations such as release, rejection, recording and alarming of people (or objects) at the entrance and exit of a building. This kind of operating system is generally composed of three parts: the entrance and exit target recognition system, the entrance and exit information management system, and the entrance and exit control execution mechanism. The front-end equipment of the system is a variety of entrance and exit target recognition devices and door lock opening and closing actuators; the transmission mode is transmitted by dedicated line or network; the terminal equipment of the system is display/control/communication equipment, and the conventional independent access controller is also adopted. The computer network implements centralized monitoring of each access controller. The entrance and exit control alarm system should be linked with the anti-theft alarm system, closed-circuit video monitoring and alarm system and fire protection system in order to effectively achieve safety precautions. The entrance and exit target recognition system can be divided into recognition of people and recognition of objects. Taking human recognition as an example, it can be divided into two types: biometric system and coded identification system.
A complete intelligent video surveillance security system, including security guard patrol alarm system, visitor alarm system and other intelligent security systems. The patrol alarm system uses the pre-programmed security patrol software to apply the pass card reader to supervise the movement status of the security personnel patrolling (whether punctuality, order of compliance, etc.), make a record, and promptly report the accident. The visitor alarm system enables the person and the visitor living in the building to make two-way conversations or visual calls. The person living in the building can remotely open or close the entrance door or the unit door in the building, and can promptly turn to the accident when the accident occurs. Security center alarm.
Other intelligent security systems are set up according to the needs of special security management tasks. Such as GPS vehicle alarm management system and 110 alarm network transmission system, it is also necessary to implement integrated management such as access control, monitoring, driving signal indication and parking billing for vehicle access roads in garages (or parking lots, etc.) The security system must have effective access control, anti-theft, surveillance control and management for important warehouses in the building.
What are the smart security products?Common intelligent security products are: smart lock, smoke alarm, gas sensor, wireless sensor alarm, intelligent host with anti-theft integrated gateway, smart camera, infrared electronic wall (infrared beam), wind and rain remote sensor, gas leak intelligent disposal robot , infrared sensor alarm, infrared electronic curtain, wireless sensor door magnet and so on.
The smart home security system provides a basic home security system for smart home residents, which is divided into front-end detectors, intelligent home controllers, network signal transmission systems, and control center control systems. In particular, the front-end detectors of the security system can be divided into door magnets, window magnets, gas detectors, smoke detectors, infrared probes, and emergency buttons.
If someone illegally invades, the corresponding detector will be triggered, and the home alarm host will immediately send the alarm signal to the cell management center or the user-specified phone, so that the security personnel can quickly alert, and the alarm host of the community management center will record these. Information is available for inspection. In addition, the smart home security system has strong adaptability and compatibility, and has different functions such as indoor intelligent alarm, perimeter automatic alarm, video monitoring, proximity card access control and internal communication. Various functions utilize the intelligent system network transmission part and The front-end home intelligent controller of the system can complete its own control based on setting its own controller and management software. At the same time, the system also provides users with various control methods for the electrical equipment in the home, no matter where the owner lives. They are able to keep abreast of the use of home appliances and control them. For example, if the owner is on a business trip, the air conditioner and electric curtains in the home can be opened by telephone or network to keep the indoor air fresh; or when the owner is at home, the remote control can be used to switch the scene lighting.

As part of the construction of smart cities, intelligent security will not only develop with the development of smart cities, but also other areas of smart city construction such as intelligent buildings, intelligent transportation, smart homes, etc. will also be the field of security products. The rapid development of smart cities has brought good news to many security companies. At the same time, due to the scale application of smart security products in the construction of smart cities, security enterprises can play a role in the construction of smart cities. For example, video surveillance, access control (including biometrics, parking management, etc.), burglar alarms, building intercom (with electronic patrol, public broadcasting are also part of the community security equipment) and other four categories of equipment will be in smart city Large areas have been used in large areas.
2. Intelligent security in the parkFrom the perspective of the type of the park, it can be divided into enterprise parks, logistics parks, industrial parks, etc. Although the functions and attributes of each park are different, the intelligent application systems basically cover access control, monitoring, alarm, perimeter, elevator control. , parking lot, electronic patrol and other systems. With the development of the economy, China's enterprise factories have seen significant improvements in both quantity and scale in the past two decades. With the expansion of the factory scale and the improvement of economic output, fire, explosion, theft and other cases have occurred frequently. It has even caused significant casualties and property damage to the factory. Therefore, modern enterprise factories are paying more and more attention to the construction of intelligent security and video surveillance systems, so as to prevent problems before they occur. Through the construction of intelligent security and video surveillance systems, enterprises can strengthen the monitoring of inbound and outbound personnel. The perimeter defense system enables security personnel to detect perimeter intruders in time to prevent and reduce theft cases; through video surveillance of workshops and production lines, Managers can intuitively understand production conditions in a timely manner; for video surveillance in hazardous work areas, personal injury accidents can be avoided and reduced.
3, campus intelligent securityThe campus comprehensive security system is of great significance in maintaining the security and stability of colleges and universities. Smart security can not only monitor the important security risks of the school in real time, but also make up for the shortage of security forces and solve problems such as inadequate monitoring. While ensuring the security of college resources, intelligent security is also conducive to cooperating with the public security department to crack down on crimes and improve the probability of solving crimes. Smart security generally includes business modules such as video surveillance, access control, vehicle management, broadcast intercom, dynamic ring management, visual patrol, public address and intercom system. The platform should adopt a platform architecture that is efficient, stable, and advanced, and has scalability and business expansion capabilities. At present, some universities with better security construction have adopted the characteristics of open architecture, component packaging, bus integration, building block development and distributed deployment to ensure that the system meets the trend of information technology development and adapts to future business applications. And the need for expansion.
4, the exhibition hall intelligent securitySince 2008, the state level has intensified the implementation of spiritual civilization construction. Museums and memorial halls are free to the whole society, and the emphasis on investment in the construction and management of museums and cultural centers is emphasized. As a result, museum construction and security system applications are also experiencing a period of rapid development. At present, most of the museum security system design is relatively simple, mainly through video for simple monitoring, making the museum's security precautions hidden. As a museum security system should be a multi-module, multi-functional, intelligent, highly sensitive combination of hardware and software. In the next three to five years, the museum's smart security applications have the following directions:
·High-definition intelligence - benchmarking events lead HD, intelligent system applications;
Multi-system integration - in addition to security subsystem interconnection, including weak integration and integration with the venue business system;
· Comprehensive security system - the integration of civil air defense, physical defense, and technical defense. It is impossible to achieve comprehensive prevention and control by relying solely on technical defense.
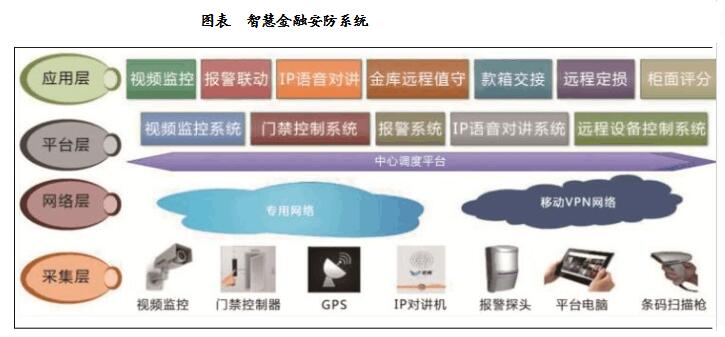
5, financial intelligence securityThe financial security intelligence is the trend of the times. When it comes to the challenges, the financial security intelligent opportunities and competition coexist. The financial security industry is constantly developing and it also puts forward various requirements for security enterprises. First, on the product side, the product performance is constantly improved, the function is continuously improved, the video image effect is continuously strengthened, the accuracy of the intelligent analysis is continuously improved, the anti-interference ability is continuously enhanced, the product quality is continuously improved, and the product shape and application occasion are improved. The second is that for the price of the product, it is required to be inexpensive, improve the functional performance of the product, but also have a higher cost performance, and the price competition will be more intense. With the upgrading of the new round of financial security system, it will bring huge potential business opportunities to the entire security market. Only by strengthening its own strength, all kinds of enterprises will respond calmly to this opportunity and challenge.
The combination of smart financial security and security industry features provides a comprehensive security system covering the “banking industry†and “insurance industryâ€. The system consists of subsystems such as “video networking systemâ€, “network alarm systemâ€, “IP voice intercom systemâ€, “access control system†and “remote loss systemâ€. Integrate the front-end point image, sound and other information of the key risk prevention areas such as the bank's business outlets, self-service banks, and banknotes, and alarm, intercom and other subsystems into a set of platforms for unified call control and management. It can meet the integrated security service application of bank video network monitoring, centralized alarm, remote emergency command, counter management, remote vault control, etc. At the same time, it can also meet the remote fixed loss service application of remote loss and centralized audit of insurance industry.
Intelligent security technology with the development and advancement of science and technology In the 21st century, the development of information technology has entered a new field. The boundary between intelligent security technology and computers is gradually disappearing. Without security technology society will appear Unrest, the advancement and development of the world's science and technology will be affected. The measurement of intelligent security technology must be carried out correctly in accordance with the national safety standards and related norms, and based on the relevant standard limits.
With the development of intelligent security technology, the workload of security intelligent information technology is getting bigger and bigger, and it is more complicated. The automatic test system (AutomaTIc Test System), which was born at the same time, has developed a digital security technology. Brand new steps. The automatic test system technology is a novel technology that combines computer technology, communication technology and detection technology organically. For nearly half a century, the combination of automatic test system technology and intelligent security technology has evolved into three periods:
(a) Combined total assembly period: An intelligent security control test system that integrates a plurality of different function program controllers with a plurality of different function input and output circuits. The development and design of this intelligent security control test system is costly and difficult to maintain, and has certain limitations in the application of intelligent security technology.
(b) Standardized interface test period: This kind of security test system uses a special interface to implement the test function change as needed. It is not only easy to set up, but also flexible in use and excellent in performance, so it has been widely used.
(c) PC (Personal Computer Based Instrument) microcomputer test period: the application of "virtual instrument" security test technology combined with computer technology and communication technology has brought a new step to the development of security system, the theory of security test technology, Application methods and many other aspects have had a huge impact.
Therefore, we can clearly see that "Virtual Instrument Security Testing Technology" will eventually become the development direction and inevitable trend of intelligent security technology.
Antenk PLCC connectors Series Sockets are low profile, thin wall sockets designed to convert plastic leaded chips to a thru-hole PCB format on a .100" centerline grid.Antenk's superior precision stamped contact design provides consistent, high retention contacts for all size chips.
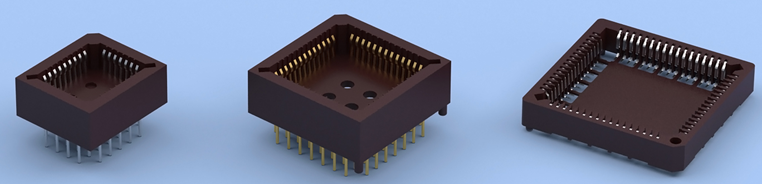
PLCC Connectors -PLCCSockets
A PLCC socket is a component that connects a chip carrier to an electronic circuit via surface-mounting or through-hole technology.
Plastic leaded chip carriers (PLCCs) are used in surface-mount technology where electronic circuits are produced, and components need to be mounted or placed directly onto a printed circuit board (PCB). The chip carrier is placed in a PLCC socket, which is either surface-mounted or features through-hole technology. A specialised tool called a PLCC extractor is needed to remove the chip carrier from the PLCC socket.
What are PLCC sockets used for?
PLCC sockets are used in surface-mount device (SMD) and surface-mount technology (SMT) applications. PLCC sockets made of heavy gauge copper alloy are compatible in high shock / high vibration applications. PLCC sockets made of rolled-leaf copper are useful in low-cost computer applications.
Types of PLCC sockets
The two primary categories of PLCC sockets are:
Surface-mount PLCC sockets, which are used in devices sensitive to heat from the reflow process. These allow for component replacement without redesigning or reworking the entire PCB.
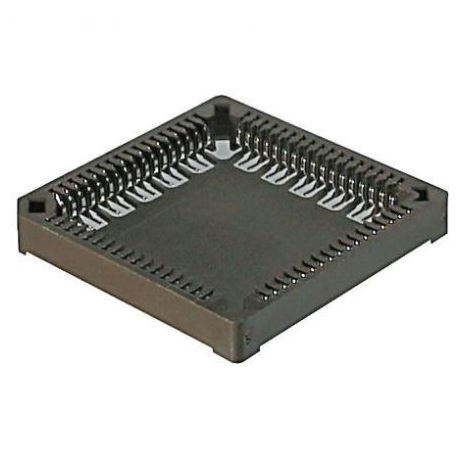
Through-hole technology PLCC sockets are necessary when a device requires stand-alone programming with flash drives or memory devices. These are also beneficial for prototyping activities where wire wrapping is required.

Plcc Socket,Plcc Connector,Plcc Socket Connector,Smd Plcc Connector,PLCC Connector DIP,PLCC Connector SMT
ShenZhen Antenk Electronics Co,Ltd , https://www.atkconnectors.com