The second most common type of electronic crime is a denial of service (DoS) attack, and about 44% of respondents have been affected.
Cisco recently acquired NetSift, a startup company that has just been established for one year. This further demonstrates that electronic crime urgently requires our high attention [2].
In combating e-crime, the usual approach is signature pattern matching, that is, whether the scanned incoming traffic contains known malicious code. As network access nodes evolved from Fast Ethernet to Gigabit Ethernet, the backbone network connection speed also increased from OC-192 (10 Gbits/s) to OC-768 (40 Gbits/s).
For this line speed, the method of using software to check the data packets is not practical, because we have almost no time to carry out the above inspection. This situation requires us to use a hardware-based packet monitor to keep up with the line speed requirements. At the same time, the number of signatures (or rules) that routers have to deal with has also grown from about 1,000 years ago to thousands of networks that currently support segmentation services.
The rules database specifies how to classify incoming data packets, subdivided services, security, load balancing, and traffic measurement. These databases contain 100,000 rules that are currently under discussion and are expected to be applicable to the network within the next year or two [3]. Since the network processor itself is a highly optimized application-specific integrated circuit (ASIC) device that performs high-speed pattern matching according to the rules specified in the database, it can well meet the requirements for combating electronic crime.
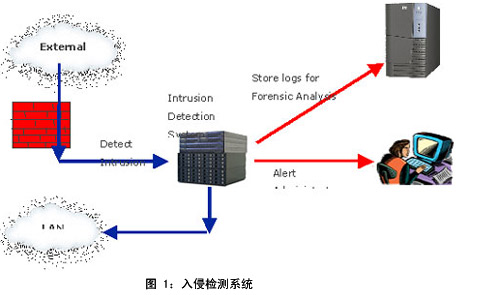
Figure 1 above shows a typical intrusion detection system that uses a network processor in IDS for signature matching.
The simple (Aho – Corasick) algorithm shown in Figure 2 below uses a state machine to search incoming traffic for all known malicious signatures. The search starts from the root node. As soon as a new character arrives, it changes state based on the arrival character. If a red node appears, it means that the signature is found and corrective actions are taken, such as avoiding the packet from entering the LAN, storing it for subsequent analysis and alerting the relevant management department.
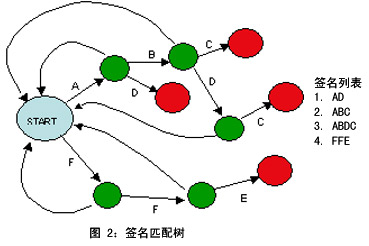
If no problem is found with the new character and it does not appear in the directory tree, the search is reset to the START node. We also use techniques such as Bloom filters to improve efficiency and thus improve the above working method [4]. The Bloom filter works as a preprocessor, allowing most of the normal traffic to pass through while identifying potentially harmful code. The potentially harmful code that is found is subject to a full inspection, reducing the load on the inspection system.
DDoS attacks
Denial-of-service (DoS) attacks prevent legitimate users from obtaining services from the resources they need. This type of attack often uses a lot of unwanted traffic to paralyze the network. A lot of useless information overloads service providers (such as web servers), which results in the inability to deliver services. DoS attacks can also cause systems to communicate with each other.
Distributed Denial of Service (DDoS) attacks use a “many-to-one†approach to attack, often controlling several zombie machines (systems that are controlled for attack without the owner’s knowledge) while The target service provider system attacks. For this attack, we propose a related solution [6]. The typical approach is to separate legitimate traffic from large amounts of DdoS traffic, ignoring illegal traffic that is designed to consume resources while continuing to serve legitimate traffic. We can achieve this by using the following technologies simultaneously:
- Redirect the client (such as a web browser) to the new server IP address and port number to identify the packet containing the real IP source address and strip out the spoofed packet. Since the redirection process can use a message authentication code (MAC) for the client's IP source address, we can identify and reject fraudulent packets.
- If the attacker attacks with a legitimate IP address, a quota system should be used to deal with it. This ensures that all client systems do not illegally consume large amounts of available resources, thereby avoiding situations where the client cannot obtain services (ie denial of service).
- Let clients (such as web browsers) "resolve" password problems. This technology allows the client (such as the web browser in this example) to undertake certain computing tasks to obtain the required services (such as downloading web pages). The relevant feasibility algorithm [5] ensures that the client requesting the service (usually the end user's computer terminal) performs the appropriate amount of computational tasks, thus avoiding overload. We force the client computer terminal to perform a small amount of calculations each time to obtain the requested service, so that it can be determined whether the hackers have controlled the zombies to attack.
In view of this, as long as the system is in danger, an alarm will be issued to the system owner and the competent authority. As long as a good IT strategy is implemented, companies can solve the problem of attackers controlling the zombies and win the fight against electronic crime.
Although we do not know in advance exactly what will happen, we use an algorithm to measure whether traffic is normal [7]. We can use the fine-grained traffic measurement function provided in the network processor to identify suspicious traffic patterns. Once discovered, we can perform quarantine checks to prevent them from entering the local network.
Attack complications
Because malicious code is easily available on the web and the attack technology is continuously upgraded, malicious code signatures are often dispersed in multiple packets (so the mechanism of detecting only a single packet no longer meets current requirements). Some signatures are still encrypted, which makes the testing more difficult. These conditions require the IDS device to be in a good state of tracking malicious code signatures in various packets while also decrypting incoming traffic. The IDS device should also encrypt normal traffic after detection so that it can reach its destination on demand.
In the past year or two, there have been several cases of combined threats (called "Blended Threats"). These attacks use a combination of a series of viruses, worms, and Trojan horses to enable malicious code to exploit the weaknesses of servers and the Internet. This mixed threat uses a variety of means to carry out proliferation attacks.
Therefore, the above attacks are more difficult to detect and prevent. These multiple attacks can occur in a variety of situations, including embedding software code in the web server and causing infection to visitors; sending spam with worm attachments; and automatically spreading the message without human intervention. This attack is best detected at the beginning of the session, otherwise it is difficult to defeat it.
In the above situation, the network processor capable of classifying the incoming malicious traffic to quickly avoid further detection will exert extremely high prevention efficiency. Due to security requirements, the requirements for NP are getting higher and higher, which brings a market for the promotion of independent ASIC devices that are specifically used for security purposes.
However, in the long run, we should not only make full use of pattern matching technology, but also incorporate fine-grained traffic management features in NP. This is a suitable method for effectively solving security problems, rather than relying on multiple ASIC security devices and allowing Each device is specifically designed to handle security threats in a specific area.
Abnormal protocol detection
When abnormal protocol detection is performed, the process of network communication sessions should be followed to identify various abnormal conditions. If an application such as a browser or a file transfer protocol (FTP) session attempts to open a port that is not related to the application protocol, we will stop the session and mark it as "needs for further inspection."
In addition, we also need to extend the above technologies and create usage descriptions in the database. If there is a session that does not match the usage description specified in the database, the IDS system will issue an alert or closely "watch" the session or force the session to terminate.
Steps to confirm intrusion
The system that verifies the intrusion on the network is divided into four phases: detection, prevention, protection, and detection of weak links. Languages ​​designed for pattern matching, such as the CPRL for signature monitoring and the Functional Programming Language (FPL) for Agere systems, can improve scan efficiency, helping to verify that an intrusion has occurred.
Although these tasks may seem burdensome, network processor or router manufacturing does not have to add a lot of computing power to all network routers to ensure network security. As long as 10% of the routers on the network are capable of content filtering, we can flexibly and skillfully place these devices in the right place to ensure that all packets passing through the network are checked [9].
to sum up
Combating e-crime often requires high-speed pattern matching to detect illegal signatures that invade the network. In addition, we should also use traffic measurement technology to monitor the subtle changes in traffic patterns to find out whether the attack session has started, although we do not understand the relevant attack mode in advance.
We use mature and stable ASIC-based IDS technology to achieve these features, because the technology supports both high-speed pattern matching, fine-grained traffic management, and statistics collection.
In summary, network processors play an important role in the fight against e-crime, because these ASIC devices are optimized to perform mode processing operations, traffic management, and statistics data collection with fine-grained performance.
References:
1. http:// ; 2.http://?id=630;
3. Author: F Baboescu and G. Varghese, taken from "IEEE / ACM Transactions on Internet" "scalable packet classification", in February 2005, First Edition, Volume 13;
4. Author: S Dharmapurikar, etc., taken from the August 2003 edition of "high-performance interconnect Proceedings (HotI)" 44 Zhi partial page 51, "Bloom filter with a parallel-depth packet inspection", Stanford, California;
5. Author: XF Wang and MK Reiter, from "in 2003 IEEE Security and Privacy Conference Proceedings (SP'03)" "with the computing tasks to prevent denial of service attacks";
6. Author:. J Xu and W. Lee, taken from "IEEE Transactions on Computer" "distributed service attack prevention, maintaining the availability of Web services," February 2003, 2nd Edition, Vol. 52, pp. 195-208 ;
7. Author: F Hao and M. Kodialam TV Lakshman, taken from the "12th IEEE International Conference on Network Protocols Memorandum (ICNP'04)" "real-time detection of hidden traffic patterns";
8. Analysis: F Hao et al., Taken from "IEEE INFOCOM 2005" 2080 to 2090 this page sheet portions "efficient manner to estimate flash memory coincides with the flow rate calculated by";
9. Analysis:. M Kodialam, TVLakshman and S. Sengupta, "configure the network nodes with content filtering, implemented network security applications."
Puff Series,Puffs Vape,Puff Flex,Puff Flex Vape
Shenzhen Zpal Technology Co.,Ltd , https://www.zpalvapes.com