Hello everyone, today we talk about xilinx FPGA bit file encryption, when your project is finally done, to the key nodes of the release, in order to prevent their own efforts to be used by others, it is best to bit encryption products.
First of all, let's take a look at the advantages of encryption. Xilinx's V6 and 7 series of FPGAs support AES256 encryption. The advantages of encryption are: 1. It can prevent others from reading back or reverse your program; 2. It can prevent changing the programmed bit file.
If you just want to prevent readback, you can simply set BITSTREAM.READBACK.SECURITY, where LEVEL1 disables readback, and LEVEL2 disables readback and reprograms the FPGA. However, if the opponent's reverse ability is very strong, for example, when the FPGA is powered on to load the bit, the logical file is used to “read†the bit file. This simple setting will definitely not work. You can use AES256 encryption at this time.
Introduction to AES Algorithm: AES is an advanced encryption standard. It is a kind of block encryption, and it is also a symmetric encryption. The block is fixed at 128 bits and the key is 128, 192, or 256 bits. AES has five encryption modes and xliinx uses CBC mode. There is a 128-bit initial vector IV (startCBC), which uses the initial vector IV to perform XOR with the first set of data and then performs an encryption operation to generate C1. C1 is used as an initial vector to perform XOR with the second set of data, and then an encryption operation is performed to generate C2. And so on, when the last set of data is encrypted, the encrypted result is stitched into the final result, C = C1C2C3...Cn. So using CBC mode 256AES requires two things, 128bit-startCBC and 256bit-AES key.
It is not finished here, and the completion of the bit encryption has not yet been certified. What if someone else burns the bit file and changes it? (Reburn new bit file). So xilinx provides HMAC authentication again. This is almost the same as checking, checking the integrity of the message. So we also need to provide 256bit-HMAC, plus 128bit-startCBC and 256bit-AES key, a total of three. These three keys can be generated on their own, or an empty .nky file can be specified and randomly generated by the software.
For example
···
Device xc7a35t;
Key 0 0f2ec1178ae0d04c8c1431afe8266d08e799b01c5c486c2567f3621f47319aaf;
Key StartCBC a6262d508c338eeab815340a7832436d;
Key HMAC d82e72733a7bd7904c802d13db37187b8ad20b972ac163470c5a4d239bce6308;
···
The encrypted AES key can be stored in the FPGA's volatile BBR or e-read only (OTP) eFUSE. BBR requires battery power and can be programmed many times. eFUSE does not require a battery, but it can only be programmed once. This uses eFUSE.
eFUSE register First look at the eFUSE register: 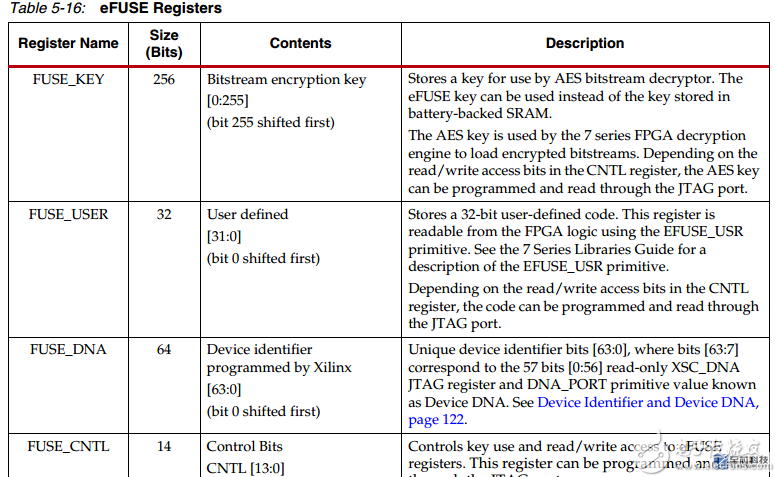
There are four registers, which are the AES key, user information, device DNA, and eFUSE control. The following special attention to the eFUSE control register: 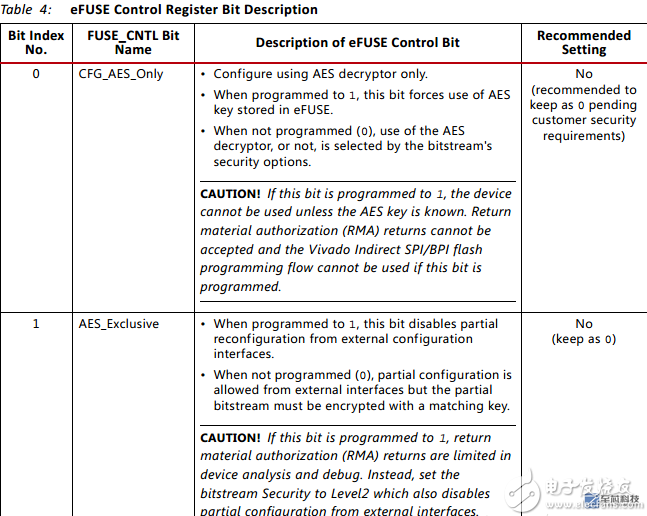
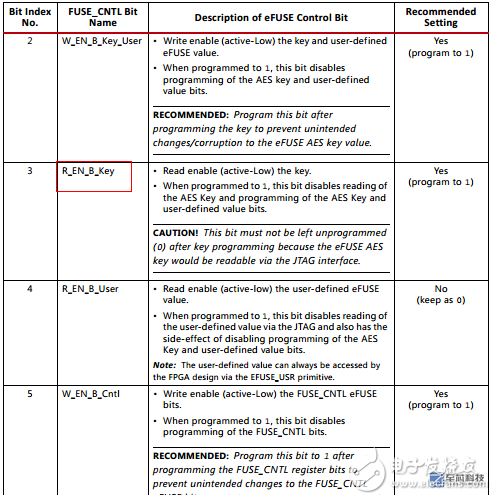
A total of 6 bits are useful. The advantages and disadvantages of the various settings are explained in detail in the table. The reference setting 101100 is used. Bit0 is very important. If it is set, the AES key will be lost and the FPGA will become a brick.
The specific steps are as follows:
Generate key and encryption bit
The following three keys can be filled in by themselves or randomly generated by the software.
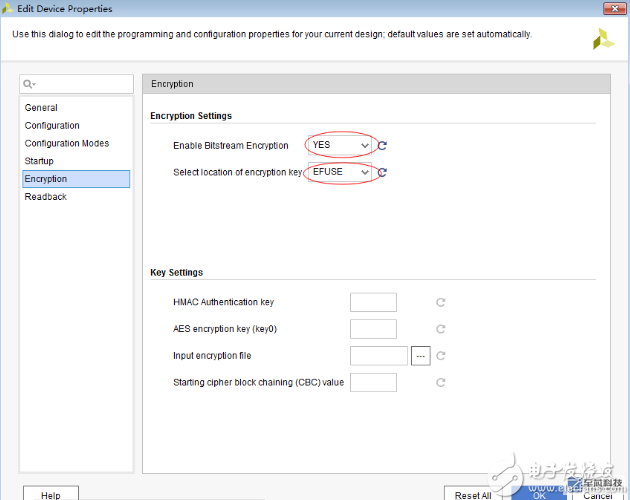
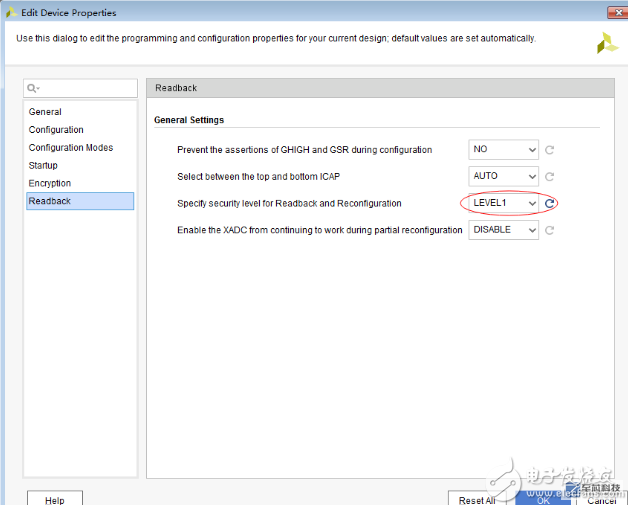
To open edit device properties, first open sythesized design or implement design, then right click on the generate bitstream
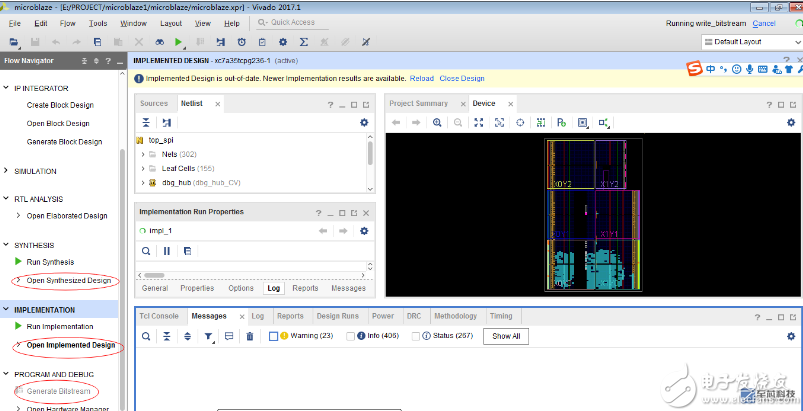
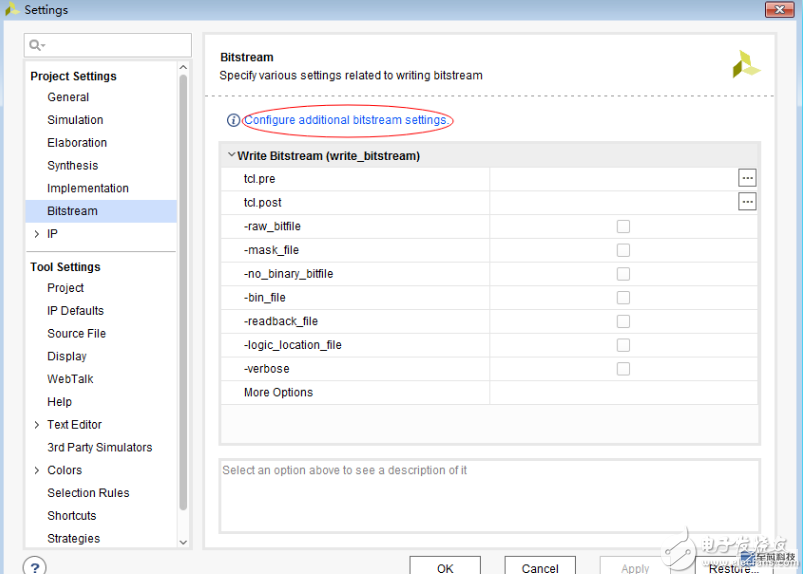
2. Download eFUSE
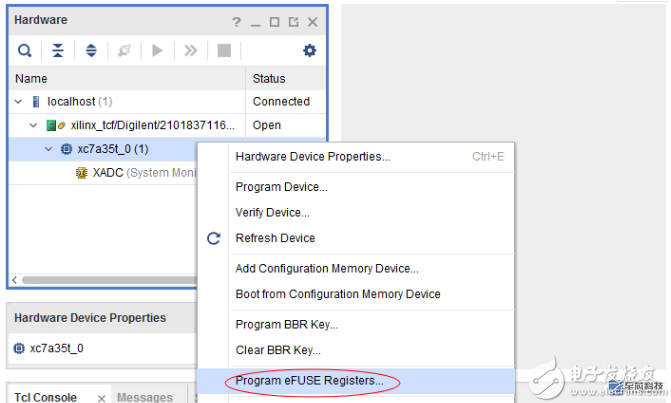
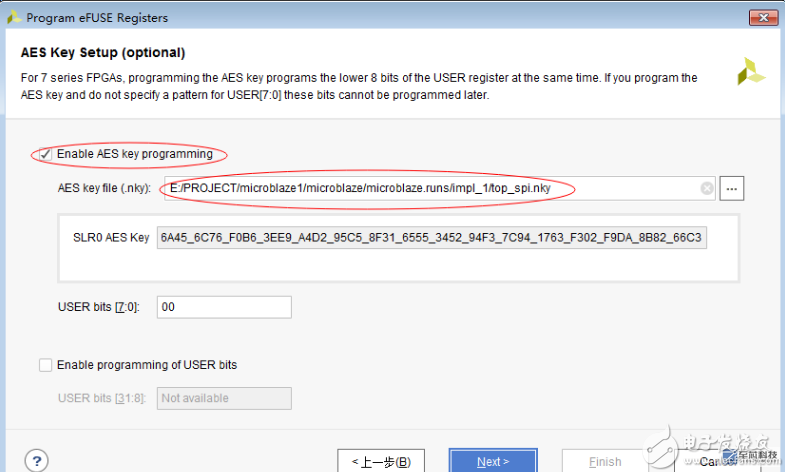
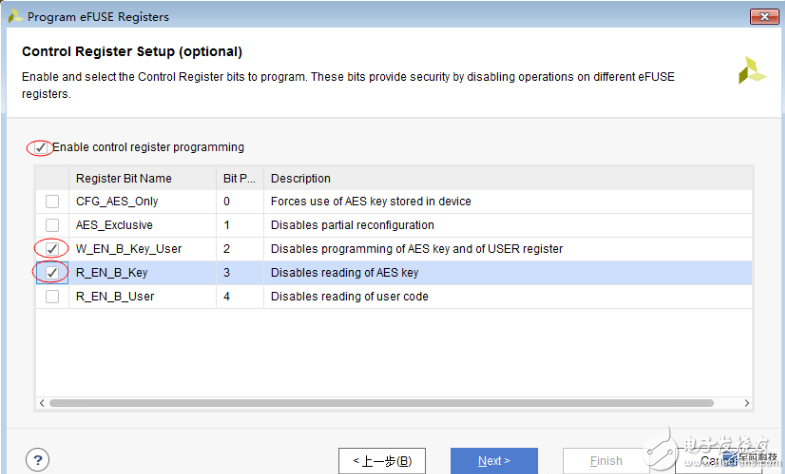
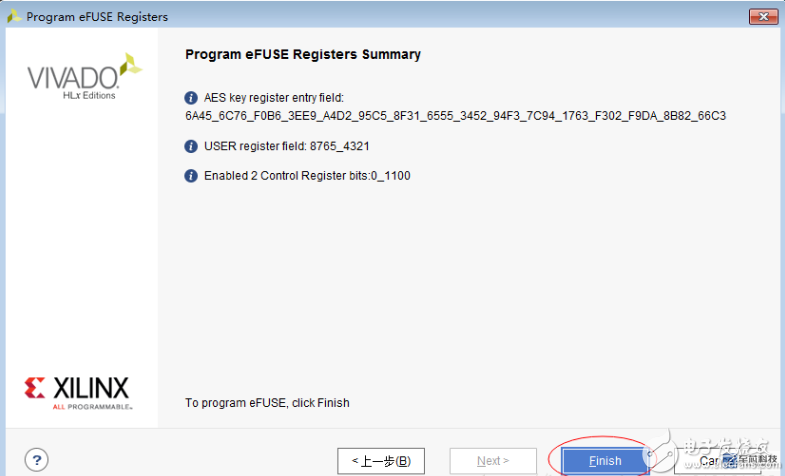
3. Write FPGA program
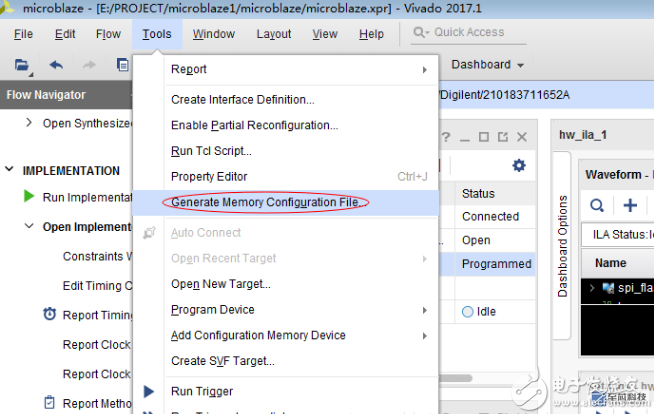
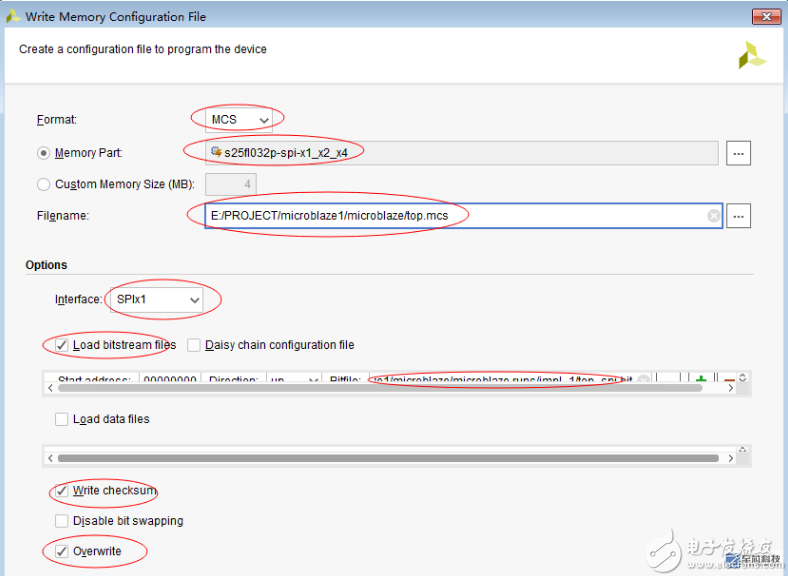
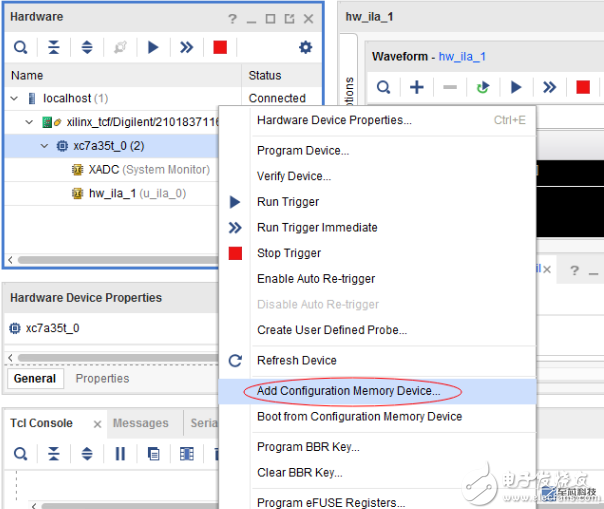
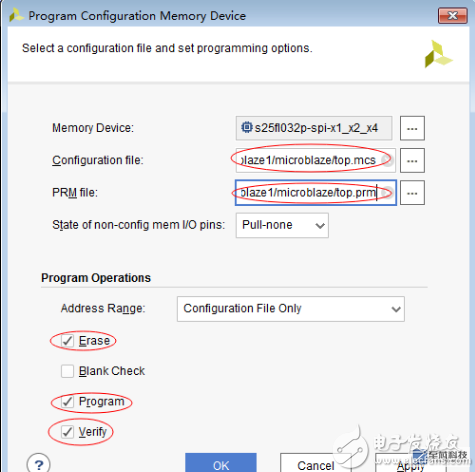
4. Verify that mcs is read and burned to another FPGA and you can see that it is not working. Of course, you can also choose to load only AES-encrypted bit files in front of the eFUSE settings. This can be verified by entering an unencrypted bit.
Interchangeable Power Adapter,Power Adapter Universal,Universal Ac Dc Adapter,Interchangeable Plug Adapter
ShenZhen Yinghuiyuan Electronics Co.,Ltd , https://www.yhypoweradapter.com