At present, most RFID readers must use more than one processor to meet the needs of the application device, and can be satisfied with a single processor by using a Convergent processor. This article will focus on the capabilities of RFID readers, explore the basic software components and server connections that must be performed on RFID readers, and provide system setup recommendations for completing designs with a single processor.
I. Overview of RFID applicationsBecause of the ability to simultaneously monitor multiple items without having to "touch" each item (for example, using a handheld barcode scanner), RFID technology enables many new applications to be implemented. The types of applications that benefit from this automated identification include various areas such as inventory control, logisTIcs management, monitoring, and billing systems.
The most common and commodity-oriented Universal Product Code (UPC) is a one-dimensional (1 D) barcode that is available on almost every item that can be purchased by the public. This bar code contains information about the item being pasted, and may include the suggested retail price of the item or the location and date of manufacture. 1 D and 2 D barcodes can also be used to track the shipping details of an item.
RFID technology replaces UPC with Product Electronic Coding (EPC) in the form of a set of bitstreams. The EPC allows at least the same type of information contained in the same set of barcodes to be automatically collected and remotely accessed, minimizing human intervention. In addition, the EPC can contain more information about the unique idenTIfying characteristics of the tagged item, even if there are many identical items. Also, unlike common bar codes, it doesn't matter which direction the item is heading or the lighting conditions around it, these items can still be detected and tracked. Fog, darkness, and even dust in the warehouse have no effect.
The following are some of the main application cases of some current RFID systems:Supermarket food shelves and boxes that track assets and provide better management of asset pools. With the ability to write tags, you can add additional information (for example: the sale deadline). In addition, automated reordering can be utilized to maintain proper stock on the shelf.
• In the library, they can be used to automate the process of borrowing books. In the past, these programs had to use a barcode scanner to read the tags one by one for identification.
• Used on clothing labels, they can be used to identify the true source of the item. By using the identification number in the tag, the item is proven to be reliable, or it is selected to investigate whether it is forged.
· In the pharmaceutical industry, they can be used to protect products and avoid the supply of counterfeit goods.
• In sports competitions, they can accurately track the progress of a runner in a long distance race.
Second, the RFID system overviewRFID uses bit-streaming radio frequency (RF) transmission to communicate, identify, classify, or track objects. Each object has its own RFID tag (also known as an answering machine: Transponder). The overall system will be equipped with a tag reader for receiving subsystems of RF energy from each tag. The built-in software of the reader is responsible for inquiring, decoding, and processing the received tag information; it also communicates with the inventory system that stores the tag database and other related information. Figure 1 shows a conceptual illustration of an RFID system.
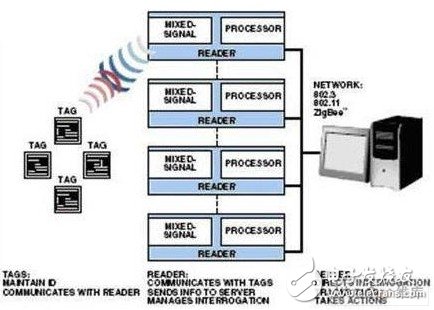
Figure 1 Simplified illustration of the RFID system
At the front end of the system, the "signal chain" starts with a small tag attached to the item; when the tag is in a specific area, the RFID reader will detect its presence and read it. Take the information conveyed in the form of a bit stream. At the back end of the system, server-based systems in the enterprise maintain and update the tag database, alert or enable other information-based processes.
RFID reader
Most RFID readers currently use more than one processor to meet the needs of the application. Usually the signal processor is connected to a set of analog-to-digital converters (ADCs) and a set of digital-to-analog converters (DACs). The network processor then communicates with the local or remote server to store or read the information.
The RFID reader provides a link between individual independent tags and the tracking/management system. In addition to its diverse size, it is usually small enough to be mounted on a counter, tripod, or wall. Depending on the application and operational conditions, multiple readers may be used simultaneously to provide adequate service capabilities in a particular area. For example, the reader network in the warehouse can ensure that all the shelves that are moved from point A to point B are 100% queried and recorded.
In general, the reader provides three main functions: two-way communication with the tag to separate each tag area; preliminary processing of the received information; connection to connect the information back to the server in the enterprise .
The D-subminiature or D-sub is a common type of electrical connector. They are named for their characteristic D-shaped metal shield. When they were introduced, D-subs were among the smallest connectors used on computer systems.
A D-sub contains two or more parallel rows of pins or sockets usually surrounded by a D-shaped metal shield that provides mechanical support, ensures correct orientation, and may screen against electromagnetic interference. The part containing pin contacts is called the male connector or plug, while that containing socket contacts is called the female connector or socket. The socket's shield fits tightly inside the plug's shield. Panel mounted connectors usually have threaded nuts that accept screws on the cable end connector cover that are used for locking the connectors together and offering mechanical strain relief. Occasionally the nuts may be found on a cable end connector if it is expected to connect to another cable end. When screened cables are used, the shields are connected to the overall screens of the cables. This creates an electrically continuous screen covering the whole cable and connector system.
ANTENK offers one of the most comprehensive lines of high reliability D-Subminiature connectors available for military, avionics, space and high reliability industrial applications.
Features of ANTENK D-Subminiature Connectors
- Standard density d-subminiature connectors
- High density d-subminiature connectors, contacts are available as well as several custom and combination versions.
- All d-subminiature connectors may be manufactured with crimp, solder cup, straight PCB and right angle PCB terminations (except solder cup terminations on High Density configurations).
Ragne of of ANTENK D-Subminiature Connectors
Standard Density solder cup, stamped & formed contact D-subminiature connectors
High Density solder cup, stamped & formed contact D-subminiature connectorsStandard Density solder cup,machined contacts D-subminiature connectors
High Density solder cup,machined contacts D-subminiature connectors
crimp & load D-subminiature connectors
IDC D-subminiature connectors
Standard Density vertical mount D-subminiature connectors
High Density vertical mount D-subminiature connectors
Standard Density right angle D-subminiature connectors
High Density right angle D-subminiature connectors
surface mount D-subminiature connectors
Slim D-sub series
D-subminiature connectors stacked D-sub series
D-Subminiature Connectors
ShenZhen Antenk Electronics Co,Ltd , http://www.coincellholder.com