Internet security has become the biggest problem for consumers in the Internet era. Nowadays, the intrusion of network viruses and cyber frauds have emerged in an endless stream. We are always worried about whether our privacy is not protected by the highest security. Is there still more and more vulnerabilities? . Nowadays, the advanced technology of artificial intelligence has been welcomed by everyone. Some people have artificial intelligence involved in network security. Artificial intelligence has great development prospects in the field of network attack and defense.
On September 21, 2017, the main event of Cyber ​​Security Week - the first International Robot Network Security Competition was officially held in Wuhan Dongxihu District. After six hours of fierce fighting, the HALFBIT team from the School of Electronic Science and Technology of the National University of Defense Technology finally won the championship. During the competition, Zhang Kai, CTO of Ever Trusty sincerity, said: "The competition system of this competition is a useful fusion attempt between the two disciplines of artificial intelligence and network security. Through this competition, we can intuitively see artificial intelligence in the network attack and defense. In the field, there is great development prospects."
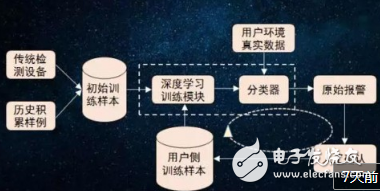
At the moment, artificial intelligence technology is developing at a rapid pace. While artificial intelligence brings convenience to the lives of the general public, artificial intelligence also brings many unknown threats in the field of network security. In order to cope with the automatic attack methods born out of the malicious application of artificial intelligence technology, Yongxin Zhicheng has jointly developed a RHG artificial intelligence attack and defense drill platform, and hosted the international robot network security competition and initiated the artificial attack. The Smart Security Application and Research Summit provides a platform for more growth for artificial intelligence network security talent.
A student of the National University of Defense Technology said in an interview with Global Intelligence, "A binary file with overflowing vulnerabilities compiled by about two hundred lines of code is thrown into the robot and the machine can be found in about 10 seconds. Vulnerability points, and it took only about 6 seconds to generate exp. What is the average time for humans to open ida? As a security person who has been in business for 17 years, I was shocked. Of course, the artificial intelligence network security application road is still very Long, today we witnessed the glory of the sunrise."
According to Zhang Kai, CTO of Yongxin Zhicheng, the questions of this artificial intelligence network security competition mainly come from the experience test questions accumulated by Yongxin Zhicheng in the process of security development, and even there are relatively wide-ranging loopholes circulating on the network. This time released 12 The title is used for the competition.
Zhang Kai said: "The competition system of this competition is a useful fusion attempt between the two disciplines of artificial intelligence and network security. Through automated procedures, the loopholes of the most popular Linux operating systems are exploited and utilized. Defense, through the analysis of attack traffic to capture features for the recurrence and defense of 0day vulnerabilities is also the mainstream of the current defense, this system of trial has an excellent practical significance. The contest applied the RHG carefully developed by Yongxin Zhicheng The platform, with the robot and robot attack and defense confrontation mode, can be said to be the first in the domestic intelligent network security competition. Through this game, we can intuitively see artificial intelligence in the field of network attack and defense, with great Development prospects."
Speaking of the WannaCry virus attack that ravaged the world some time ago, although Zhang Kai, the head of the main technology, did not lead the topic to the virus itself, but talked about the cultivation of security talents. Zhang Kai said: "People are the root of security, and the strategy of a strong system and a powerful computer is hard to work. We often feel that the talents in the security field are scarce, and there are too few people involved. We hope that the whole big platform of e Spring and Autumn will train talents, and we must promote the construction of network security in an all-round way, so that more people can understand network security and cultivate everyone's awareness of network security."
As Hao Yeli, president of the National Innovation and Development Strategy Research Association, said in the comprehensive review after the competition and the summit: "We can see through this game that artificial intelligence has great development space in the field of network security. However, the road is long and the artificial intelligence hacker is just getting started. There is still a long way to go before the network security is intelligent. We believe that there is a long way to go, and we hope that this seedling can grow into a network security field as soon as possible. Giant trees."
3.5mm Wire To Board Connectors
3.5mm Wire To Board Connectors.Standards
Wire-to-board connectors carry approvals from various national and international organizations. In North America, they often bear marks from Underwriters Laboratories (UL) and/or the Canadian Standards Association (CSA).
A wire to board connector for the European marketplace should comply with the Restriction of Hazardous Substances (RoHS) and Waste Electrical and Electronic Equipment (WEEE) directives from the European Union (EU). Wire-to-board connectors that comply with other requirements are also available.
BS 9526 N0001 - Specification for multi-contact edge socket electrical connectors.
3.5mm Wire To Board Connectors
ShenZhen Antenk Electronics Co,Ltd , https://www.atkconnectors.com